Computer Science
Undergraduate Programs
Stevens offers undergraduate majors in Computer Science and Cybersecurity. Each is specifically designed to train the high-end IT professionals who can take advantage of trends in the IT industry and gain entry into a challenging and rewarding career path in software development and systems analysis.
Science Requirement
All majors must take one of these science sequences, each consisting of two science courses and a science laboratory:
|
Science I |
Science II |
Science Lab |
|
|
Physics |
PEP 111 Mechanics |
PEP 112 Electricity and Magnetism |
PEP 221 |
|
Chemistry |
CH 115 General Chemistry I |
CH 116 General Chemistry II |
CH 117 |
|
Chemistry & Biology |
CH 115 General Chemistry I |
BIO 281 Biology & Biotechnology |
CH 117 |
|
Chemistry & Biology |
CH 115 General Chemistry I |
BIO 281 Biology & Biotechnology |
CH 282 |
|
Physics & Biology |
PEP 111 Mechanics |
BIO 281 Biology & Biotechnology |
CH 282 |
Humanities Requirement
One humanities course must be HSS 371 Computers and Society or HPL 455 Ethical Issues in Science and Technology. In addition, students must follow the requirements of the College of Arts and Letters:
- All freshmen must take CAL 103 Writing and Communication and CAL 105 CAL Colloquium.
- At least one humanities course must be at the 100 or 200 level and at least one course must be at the 300 or 400 level.
- Courses must be taken in at least two of the four disciplines of Literature, Philosophy, History, and Social Science.
Physical Education Requirement
- All students must complete a minimum of four semesters of Physical Education (P.E.). A large number of activities are offered in lifetime, team, and wellness areas.
- All PE courses must be completed by the end of the sixth semester. Students can enroll in more than the minimum required P.E. for graduation and are encouraged to do so.
- Participation in varsity sports can be used to satisfy up to three semesters of the P.E. requirement.
- Participation in supervised, competitive club sports can be used to satisfy up to two semesters of the P.E. requirement, with approval from the P.E. Coordinator.
Getting Started
Study begins with a three-course sequence (CS 115, CS 284, and CS 385) that teaches the fundamentals of computer programming. Most students will take these courses in sequence in their first three semesters. Students who enter with a limited background in computer programming or who want reinforcement of fundamental concepts should take CS 110 in the first semester followed by the sequence 115-284-385 in semesters II though IV. Students who take the Honors sequence of 181-182 will skip the 115-284-385 sequence; the two Honors courses are equivalent to the standard three-course sequence.
Advanced Placement
Students who receive a score of 4 or 5 on the computer science advanced placement exam receive credit for one technical elective and are encouraged to take CS 181 in semester I. Students who receive a score of 6 or 7 on the International Baccalaureate (IB) computer science exam, Standard Level, are treated similarly. Students who receive a score of 6 or 7 on the IB computer science exam, High Level, receive credit for one free elective course, are exempted from CS 115, CS 284, and CS 181, and start in CS 182.
Bachelor of Science in Computer Science
Besides its technical rigor, the Computer Science major is distinguished by its flexibility. In the senior year, a student can choose from a large number of elective courses.
The Computer Science Department is also the home to world-class research in areas such as computer security, vision and visualization, and data mining. The quality of this research is demonstrated by the publication and funding records of the faculty of the department. Undergraduate students are encouraged to get involved with faculty in their research. Indeed, while graduate students come from all over the world to be involved with research, some undergraduates choose to stay at Stevens for their graduate work, pursuing Ph.D. research with the faculty they came to know during their undergraduate studies.
Computer Science Requirements
The program requires the following courses:
Mathematics
- MA 121 Differential Calculus
- MA 122 Integral Calculus
- MA 123 Series, Vectors, Functions, and Surfaces
- MA 124 Calculus for Functions of Two Variables
- CS 135 Discrete Structures
- MA 222 Probability and Statistics
- MA 331 Intermediate Statistics
- CS 334 Automata and Computation
Computer Science
- CS 115 Introduction to Computer Science
- CS 146 Introduction to Web Programming and Project Development
- CS 284 Data Structures
- CS 306 Introduction to IT Security
- CS 347 Software Development Process
- CS 383 Computer Organization and Programming
- CS 385 Algorithms
- CS 392 Systems Programming
- CS 423 Senior Design I
- CS 424 Senior Design II
- CS 442 Database Management Systems
- CS 443 Database Practicum
- CS 485 Societal Impact of Information Technologies
- CS 492 Operating Systems
- CS 496 Principles of Programming Languages
- CS 511 Concurrent Programming
- Choose one: CS 522 Mobile Systems and Applications, or CS 546 Web Programming, or CS 548 Enterprise Software Architecture and Design
Management
- BT 353 Project Management
Electives
Electives fall into four categories: science/math, software development, technical, and free. Students must take at least two science/math electives and one software development elective. The number of required technical and free electives is determined by how the student starts his/her program. Students who start with CS 115 must take two technical electives and two free electives. Students who start with CS 110 must use CS 110 as a technical elective, leaving one more technical elective and two free electives. Students who start with CS 181 must take two technical electives and three free electives.
Not every science or math course may be counted as a science/math elective. Students should consult their advisor or the department web site to learn of any restrictions.
The software development elective may be chosen from the following list of courses that involve substantial programming assignments:
- CS 537 Interactive Computer Graphics
- CS 541 Artificial Intelligence
- CS 558 Computer Vision
- CS 546 Web Programming
- CS 516 Compiler Design
- CS 521 TCP/IP Networking
- CS 522 Mobile Systems and Applications
- CS 526 Enterprise and Cloud Computing
- CS 548 Enterprise Software Architecture and Design
- CS 549 Distributed Systems and Cloud Computing
Please consult the department web site for the rules that define technical electives.
Despite the description "free elective," not every course may be counted as a free elective; in particular, courses that are similar to required courses may not be taken as free electives. Students should consult their advisor or the department web site to learn of any restrictions.
Minor in Computer Science
You may qualify for a minor in computer science by taking the courses indicated below. Enrollment in a minor means you must meet the Institute's requirements for minor programs. As many as five of the seven courses may be double-counted toward both your minor and your major, assuming that your major accepts those five courses. Only courses completed with grade of C or better are accepted towards a student's minor.
The minor includes these four courses:
- CS 115 Introduction to Computer Science
- CS 135 Discrete Structures or MA 134 Discrete Mathematics
- CS 284 Data Structures
- CS 385 Algorithms
plus any two CS courses numbered 300 or higher; these courses must each be 3 or more credits. No course may duplicate another; specifically, students may not count toward the minor CS 501, CS 570, or CS 590; also, students may not count toward the minor both courses in each of the following pairs: CS 383 and CS 550, CS 492 and CS 520, CS 496 and CS 510, CS 442 and CS 561.
Because the minors offered by the Computer Science Department—computer science, cybersecurity, game development—overlap substantially, it is prohibited to take more than one.
Bachelor of Science in Cybersecurity
The Bachelor of Science program in Cybersecurity is structured to provide students with security expertise within the context of a broad education. A solid education in security requires not only a strong focus in science and computer science in particular (e.g., need for robust implementation and software validation), but must also incorporate some aspects of engineering and technology management. While cryptographers strive to develop the best security solution possible, actual implementations of theoretical concepts often fail due to technological limitations, cost restraints, and human factors that were not part of the initial design process. For a solution to gain practical relevance, the end user must be able and willing to use it. From an economical point of view, a solution must provide a substantial monetary benefit to the customer. In order to allow for these complex issues to be better addressed, an education in cybersecurity must integrate science, technology, and management.
Cybersecurity Requirements
The program requires the following courses:
Mathematics
- MA 121 Differential Calculus
- MA 122 Integral Calculus
- MA 123 Series, Vectors, Functions, and Surfaces
- MA 124 Calculus for Functions of Two Variables
- CS 135 Discrete Structures
- MA 222 Probability and Statistics
- CS 334 Automata and Computation
Computer Science
- CS 115 Introduction to Computer Science
- CS 284 Data Structures
- CS 146 Introduction to Web Programming and Project Development
- CS 347 Software Development Process
- CS 383 Computer Organization and Programming
- CS 385 Algorithms
- CS 392 Systems Programming
- CS 425 Cybersecurity Capstone I
- CS 426 Cybersecurity Capstone II
- CS 442 Database Management Systems
- CS 443 Database Practicum
- CS 485 Societal Impact of Information Technologies
- CS 488 Computer Architecture
- CS 492 Operating Systems
- CS 496 Principles of Programming Languages
- CS 511 Concurrent Programming
- CS 521 TCP/IP Networking
- CS 595 Information Security and the Law
Cybersecurity
- CS/MA 503 Discrete Mathematics for Cryptography
- CS 306 Introduction to IT Security
- CS 576 Secure Systems
- CS 577 Cybersecurity Laboratory
- CS 578 Privacy in a Networked World
- CS 579 Foundations of Cryptography
Security Electives
The program provides one CS elective and two security electives. The following courses are approved as security electives. Note that undergraduates must meet minimum GPA requirements to enroll in 600-level courses:
- CS 594 Enterprise Security and Information Assurance
- CS 665 Network Forensics
- CS 675 Threats, Exploits, and Countermeasures
- CS 693 Cryptographic Protocols
- CS 695 Host Forensics
- CPE 592 Multimedia Network Security
- EE 584 Wireless Network Security
- SSE 623 Systems Security Architecture and Design
Other Cybersecurity electives may be approved at the discretion of the program director.
Minor in Cybersecurity
You may qualify for a minor in cybersecurity by taking the courses indicated below. Enrollment in a minor means you must meet the Institute's requirements for minor programs. As many as five of the seven courses may be double-counted toward both the minor and your major, assuming that your major accepts those five courses. Only courses completed with grade of "C" or better are accepted towards a student's minor.
The minor includes these seven courses:
- CS 115 Introduction to Computer Science
- CS 135 Discrete Structures
- CS 284 Data Structures
- CS 385 Algorithms
Plus one of the following tracks:
- CS 503 Discrete Mathematics for Cryptography
- CS 578 Privacy in a Networked World
- CS 579 Foundations of Cryptography
- CS 306 Introduction to IT Security
- CS 576 Secure Systems
- CS 577 Cybersecurity Laboratory
This minor is closed to Computer Science majors
Because the minors offered by the Computer Science Department—computer science, cybersecurity, game development—overlap substantially, it is prohibited to take more than one.
Minor in Game Development
The department offers a minor in game development; there is no game development major. The minor includes the minimum set of courses necessary for a student to go from zero to having substantial preparation in the design and construction of computer games. Since this goal requires knowledge of graphics and artificial intelligence, which are both substantial domains, the minor includes eight courses. As many as six of the eight courses may be double-counted toward both the minor and your major, assuming that your major accepts those six courses.
This minor is closed to majors in Computer Science or Cybersecurity. The minor includes these courses:
- CS 115 Introduction to Computer Science
- CS 135 Discrete Structures
- CS 284 Data Structures
- CS 385 Algorithms
- CS 585 Introduction to Game Development
- CS 537 Interactive Computer Graphics
- CS 587 Game Engine Design
- CS 541 Artificial Intelligence or CS 586 Machine Learning for Game Design
Because the minors offered by the Computer Science Department—computer science, cybersecurity, game development—overlap substantially, it is prohibited to take more than one.
Graduate Programs
The Computer Science Department offers six master's degrees, several graduate certificates, an engineer degree, and a doctoral degree.
- Master of Science in Computer Science: The MS/CS is the flagship graduate program. It is designed to be flexible in allowing students to combine several areas of concentration, such as software engineering, cybersecurity, and databases and service-oriented architecture. Ph.D. students who do not already have a M.S. degree should consider pursuing a M.S. in Computer Science to develop breadth before their Ph.D. studies.
- Master of Science in Service-Oriented Computing: The MS/SOC is an accelerated professional education program that develops the skills set required for developing Web and internet applications, particularly tailored for those with little or no previous programming experience. An optional introductory course teaches introductory programming using a language such as Visual Basic. Subsequent courses teach Web programming using PHP and JavaScript, and distributed programming using frameworks such as .NET. Other courses teach software requirements engineering, human computer interaction, information architecture for Web site design, and service-oriented architecture (SOA).
- Master of Science in Enterprise and Cloud Computing: The MS/ECC is intended to educate high-end IT professionals with an interest in enterprise computing. Students learn about distributed computing from both the reliability and security points of view, including service-oriented architecture (SOA). This program has a particular emphasis on systems administration and governance. A typical back-end setup will involve several virtualized servers, running heterogeneous guest operating systems on top of hypervisors, organized in a highly available cluster. Data processing and Web service applications will have service level agreements (SLAs) that must be honored. This program develops the skills sets for the professionals who administer such operations.
- Master of Science in Cybersecurity: The MS/CyS is a rigorous program in the art and practice of cybersecurity, including fundamentals of cryptography, and threats and defenses for secure systems. The emphasis in this program is on deep technical skills that may be complemented with courses in security management, in addition to the security courses suggested for the MS/CS which emphasize broad principles and security administration.
- Master of Science in Game Design and Simulation Programming: This degree exposes students to the fundamentals of interactive game design, state-of-the-art graphics and animation and behavior modeling, and the methodologies for game development. The program also provides the skills and environment needed to be a successful member of the gaming community. The program prepares students for positions in the gaming industry as well as in industrial, government, education and research organizations that use simulation, visualization, automated training and "edutainment".
- Master of Science in Media and Broadcast Engineering: Media and broadcast engineering lies at the intersection of audio/video processing, networking, software design, and complex system integration. The Master of Science in Media and Broadcast Engineering provides students with a comprehensive foundation in all aspects of media production, delivery, and management, and prepares them for relevant careers as media and broadcast engineers, network managers and developers, streaming media developers, and project managers for broadcast networks. It provides similar education and opportunities to professionals in the field who wish to enhance their skillsets. It also covers media engineering in emerging media publishing channels such as through the Internet and mobile applications.
- Graduate Certificate: A graduate certificate typically consists of four graduate courses in a targeted area of study. The courses for a graduate certificate also may be used towards another graduate degree, such as a master's degree.
- Engineer in Computer Science: The degree of Engineer in Computer Science is for students who already have a Master degree in computer science or a closely related field and who wish to continue to study computer science deeply at an advanced level, but who do not wish to or cannot make the time commitment necessary for the PhD degree. The degree requires 30 credits of computer science beyond the MS degree. Nine to twelve of these credits must be for a single long-term project on an advanced computer science topic (course CS 950).
- Ph.D. in Computer Science: The doctoral degree is a program of full time on-campus study only, aimed at preparing the student for a career in computer science research.
Master of Science - Computer Science
Degree Requirements
- Completion of at least thirty credits at the graduate level (500 level and above), with a minimum grade of C and a minimum GPA of 3.00.
- At least twenty-one credits must be from computer science courses, identified by the CS prefix.
- At least three of the courses must be drawn from this set: CS 510, CS 511, CS 513, CS 520, CS 521, CS 522, CS 524, CS 526, CS 537, CS 541, CS 545, CS 546, CS 548, CS 549, CS 561, CS 573, CS 578, CS 600, CS 677, CS 694.
- The remaining nine credits can be from computer science or any other disciplines.
Some students may seek to take electives that form a focused area of study. Accordingly, several suggested focus areas of logically related electives are defined including:
- Cloud Computing
- Databases
- Gaming and Simulation
- Mobile Systems
- Modeling, Simulation, and Visualization
- Network and Systems Administration
- Secure Systems
- Software Development
- Visual Computing and Information Extraction
- Web Application Development
See the Computer Science Department web site for definition of these focus areas.
Master of Science – Media and Broadcast Engineering
Degree Requirements
1. Completion of at least thirty credits at the graduate level (500 level and above), with a minimum grade of C and a minimum GPA of 3.00.
2. Three core courses that are mandatory in all tracks.
3. Three courses from a chosen track.
4. Two technical electives from any track.
5. Two general electives that can be any Stevens course at the 500 level or above, including a relevant M.S. thesis in one of the program’s home departments.
Track I: Signal Processing and Data Communication
As a traditional branch of Electrical and Computer Engineering, this track provides fundamental knowledge and skills related to audio and video processing, information compression, data communication and networking, which are enabling technologies in the media and broadcasting industry.
Track courses:
- CPE 645 Image Processing and Computer Vision
- CPE 548 Digital Signal Processing
- CPE 591 Introduction to Multimedia Networking
- EE 585 Physical Design of Wireless Systems
- EE 626 Optical Communication Systems
- EE 670 Information Theory and Coding
Elective courses:
- CS 537 Interactive Computer Graphics
- CS 558 Computer Vision
Track II: Software Infrastructure for Media and Broadcast Engineering
This track covers aspects of software design and development that are critical for media and broadcast engineering, including networking, distributed and cloud computing, web programming, programming for mobile systems, databases, and algorithms/
Track courses:
- CS 522 Mobile Systems and Applications
- CS 524 Introduction to Cloud Computing
- CS 526 Enterprise and Cloud Computing
- CS 546 Web Programming
- CS 548 Enterprise Software Architecture & Design
- CS 554 Web Programming II
Elective courses:
- CS 520 Introduction to Operating Systems
- CS 561 Database Management Systems I
- CS 570 Introduction to Programming, Data Structures, and Algorithms
- CS 590 Algorithms
- CS 600 Advanced Algorithm Design and Implementation
- CS 615 Systems Administration
Master of Science - Service-Oriented Computing
As IT becomes more and more ubiquitous, in e-commerce and e-government, there is an exploding demand for the wide range of expertise in IT and software development that is needed to meet the demands of the modern information economy. In particular, there is a need for domain-specific experts who are conversant both in information technology and software skills, and also have a facility for the appropriate applications of these technologies in a particular field.
Technologies such as Web services are facilitating a view of software as "services," much more fine-grain than the normal view of software libraries, which may be used for heavyweight inter-enterprise application integration, but may also be used for very flexible lightweight rapid development of new applications. We are seeing the emergence of frameworks that domain experts in that sector can use, not just to compose together services, but also to synthesize new applications. This synthesis may be done using scripting languages or domain-specific programming languages and protocols. This is related to an emerging phenomenon of "situational programming," where lightweight applications must be developed rapidly and relatively easily. This goes somewhat beyond simple "mash-ups" on the Web, but such applications often do not require the depth of skill and management that large software projects entail.
The Master of Science in Service-Oriented Computing, program is an accelerated professional education program that provides domain experts with the skill sets that they need in order to use and manage the IT that is being deployed globally today. Students may have little or no background in software development, but they are already, or want to be, a professional in a particular field with IT skills. The program provides very focused training in the skill sets that are required to make students technically capable of taking existing frameworks and using them to develop new client-specific applications.
The focus of the program is very much on front-end skills:
- Requirements acquisition and analysis
- Human-computer interaction
- Web design and information architecture
- Ethical and privacy issues
The kinds of tasks that students pursue range all the way from designing and implementing Web pages, to developing distributed collaborative applications with sophisticated database back-ends.
The program provides a very focused path for obtaining the basic software development skills that graduates will require. The sequence starts with an optional introductory programming course, SOC 605, that teaches fundamental problem-solving skills in the context of learning a programming language that is geared to end-user applications (e.g., C#). This course may be omitted for those that have already had an introductory programming course, although students with such a background may still be interested in taking the course in order to learn C#. A successor course, SOC 606, teaches basic software engineering skills and best practices for Web-Based applications, particularly for three-tier client-server applications using a Web Server as a front-end to a database, using C# and .NET. Other core courses teach the fundamentals of a service oriented architecture (SOA) and workflow, for modern enterprise systems with Web service frontends, as well as the fundamentals of human computer interface design and information architecture. Elective courses are available in privacy, data mining, health informatics and enterprise security. Up to three elective courses may be taken in other disciplines to which students wish to apply the principles of service oriented computing.
This is called a program in service-oriented computing (informatics is also a term that is sometimes used) because service-oriented architectures (SOA) are the emerging basis for the frameworks that graduates will be using to develop domain-specific end-user applications. Web and distributed programming, along with basic software engineering and human-computer interaction (HCI) skills, are an important part of the necessary skills sets.
Degree Requirements
- Completion of at least thirty credit hours of study at the graduate level (500-level and above), with a minimum grade of C and a minimum GPA of 3.00.
- Completion of all of the core courses. Note that SOC 605 may be required as a prerequisite to SOC 606, depending on the student's background.
Core Courses
- SOC 510 Human Computer Interaction
- SOC 542 Enterprise Software Architecture and Design
- SOC 606 Introduction to Developing Internet Applications or CS 526 Enterprise and Cloud Computing or CS 546 Web Programming
- SOC 611 Fundamentals of Service Oriented Computing or CS 561 Database Management Systems I
Master of Science - Enterprise and Cloud Computing
The MS/ECC program is intended to educate high-end IT professionals with an interest in enterprise computing. Students will learn about distributed computing from both the reliability and the security points of view. They will learn about distributed computing "in the large," including enterprise application integration and service-oriented architectures (SOA). They will build on skills learned in courses in databases and systems programming for enterprise computing to learn how to administer server back-ends that are the crux of modern SOA. This will involve ensuring that applications meet their goals in terms of performance, reliability, security, and privacy. A typical back-end setup will involve several virtualized servers, running heterogeneous guest operating systems on top of hypervisors, organized in a highly available cluster. Data processing and Web service applications will have service level agreements (SLAs) that must be honored. The administrator must be able to respond to performance issues by dynamically reallocating resources between applications, while at the same time responding to component failures, and potentially also security attacks. They will also need to ensure that procedures are followed for ensuring privacy guarantees, some of which will be mandated by legislation. They may work with company lawyers to define what these procedures are. The MS/EC program includes a course in security administration that covers technical, management, and legal aspects of enterprise security and privacy, including security governance, privacy concerns, and best practices for secure systems.
As well as developing technical skills, students will develop skills in client-facing, business cases, and project management. Such skills are expected in general, and particularly for enterprise IT professionals. A course in enterprise software engineering exposes students to best practices in enterprise architecture integration and SOA. Courses in software engineering teach the principles and theory of programming-in-the-large, including teamwork, problem solving, and agile software development methods. The courses are modeled on business software development practices, so that students experience a transition from academia to business. Students produce useful, well-engineered software products, applying software engineering techniques, ethical principles, and generally accepted software practices.
Degree Requirements
- Completion of at least thirty credit-hours of study at the graduate level (500-level and above), with a minimum grade of C and a minimum GPA of 3.00.
- All of the core courses must be completed. The remaining courses should come from a list of approved electives, or with the approval of the program director.
Core Courses
- CS 522 Mobile Systems and Applications or CS 526 Enterprise and Cloud Computing
- CS 548 Enterprise Software Architecture and Design
- CS 549 Distributed Systems and Cloud Computing
- CS 561 Database Management Systems I or CS 594 Enterprise Security and Information Assurance
Elective Courses
Students must choose an additional five courses for their MS/ECC study plan. At least two of these courses must be Computer Science courses i.e., with the CS prefix. Up to three of the courses can be from free electives from any other discipline, including Computer Science, Software Engineering, or Management and Information Systems, with the approval of the program director. Below are some suggested electives.
- CS 503 Discrete Mathematics for Cryptography
- CS 506 Introduction to IT Security*
- CS 513 Knowledge Discovery and Data Mining
- CS 520 Operating Systems
- CS 521 TCP/IP Networking
- CS 522 Mobile Systems and Applications
- CS 524 Introduction to Cloud Computing
- CS 544 Health Informatics
- CS 546 Web Programming
- CS 561 Database Management Systems I
- CS 562 Database Management Systems II
- CS 578 Privacy in a Networked World*
- CS 579 Foundations of Cryptography
- CS 609 Data Management and Exploration on the Web
- CS 615 Systems Administration
- CS 629 Advanced Internet Protocols
- CS 665 Network Forensics
- CS 675 Threats, Exploits, and Countermeasures
* Students who take CS 506 and CS 578 will be eligible for a graduate certificate in Enterprise Security and Information Assurance
- MGT 600 Financial and Managerial Accounting
- MGT 606 Managerial Economics
- MGT 623 Financial Management
- MIS 662 Legal Issues for the IT Professional
- MIS 675 Analyzing Technology Risks
- SSW 533 Software Cost Estimation and Metrics
- SSW 540 Fundamentals of Software Engineering
- SSW 565 Software Architecture and Component-Based Design
- SSW 567 Software Testing, Quality Assurance, and Maintenance
Master of Science - Cybersecurity
Security breaches such as the Code Red, Sobig, and MyDoom worms have cost several billion dollars to the global economy in recent years. Conservative estimates by security experts are that millions of residential computers are "zombies" (or “bots”) taken over by attackers unbeknownst to their owners, organized into "bot-nets," and used routinely for spamming everyone that uses the Internet. Denial of service attacks have been staged against major corporations that rely on network access, such as eBay, as well as against the root servers for the internet Domain Naming System (DNS), using bot-nets whose "services" that can be purchased on the black market for just a few hundred dollars. Criminal gangs are hiring expert programmers to break into law enforcement databases to learn the names of informants. Consumers are becoming more and more reliant on computer systems, even for sensitive activities like home banking, while companies and governments are exposing themselves to potential attacks due to the need to establish and maintain a "Web presence." On the legislative level, increasing privacy concerns are giving rise to legislation of which companies must be aware and to which they must be able to adapt.
In response to these trends, Stevens has developed a graduate program in cybersecurity that provides deep and rigorous training in cybersecurity to IT professionals who already have a background in computer science, computer engineering, or other closely related discipline in the information sciences. The program aims to provide a nationally recognized credential for cybersecurity professionals. Academically inclined graduates of this program will also be well poised to pursue Ph.D. study in cybersecurity, should they so choose. The program provides a rigorous education in the foundations of security and privacy, including cryptography and secure systems.
Degree Requirements
Completion of at least thirty credit-hours of study at the graduate level (500-level and above), with a minimum grade of C and a minimum cumulative GPA of 3.00. The seven core courses listed below must be completed.
Beyond the core courses listed below, students may choose from a list of approved electives posted on the department web site.
Core Courses
- CS 520 Introduction to Operating Systems
- CS/MA 503 Discrete Mathematics for Cryptography
- CS 573 Fundamentals of Cybersecurity
- CS 578 Privacy in a Networked World
- CS 579 Foundations of Cryptography
- CS 600 Advanced Algorithm Design and Implementation
- CS 675 Threats, Exploits, and Countermeasures
- or CS 665 Network Forensics
CS 520 and CS 600 may be replaced by electives if the student already has taken these courses as an undergraduate.
Master of Science - Game Design and Simulation Programming
This degree exposes students to the fundamentals of interactive game design, state-of-the-art graphics and animation and behavior modeling, and the methodologies for game development. The program also provides the skills and environment needed to be a successful member of the gaming community. The program prepares students for positions in the gaming industry as well as in industrial, government, education and research organizations involved in simulation, visualization, automated training and "edutainment". The degree is appropriate for recent graduates in computer science, persons working in electronic media and entertainment, gaming studios, government employees involved in computer simulations and training, as well as people going after their dream to "start a gaming company".
Degree Requirements:
- CS 522 Mobile Systems and Applications
- CS 537 Interactive Computer Graphics
- CS 539 Real time Rendering, Gaming, and Simulation Programming
- CS 541 Artificial Intelligence
- CS 543 Principles of Computer Mediated Entertainment or CS 597 User Experience Design and Programming
- CS 545 Human Computer Interaction
- CS 585 Introduction to Game Development
- CS 586 Machine Learning for Game Design
- CS 587 Game Engine Design
- CS 638 Advanced Computer Graphics or CS 677 Parallel Programming for Many-core Processors
Graduate Certificate Programs
The Computer Science department offers graduate certificate programs to students meeting the regular admission requirements for the master's program. Each certificate program is self-contained and highly focused, comprising 12 or more credits. Courses taken for a Graduate Certificate may also be used toward a master's degree.
Cloud Computing
- CS 522 Mobile Systems and Applications
- CS 548 Enterprise Software Architecture and Design
- CS 549 Distributed Systems and Cloud Computing
- CS 594 Enterprise Security and Information Assurance
Databases
This program provides a firm grounding in enterprise architecture, particularly as supported by modern database management systems and platforms such as Web services. Students may also focus on data mining, including both algorithms and applications of existing data mining tools.
- CS 561 Database Management Systems I
- CS 562 Database Management Systems II
- CS 546 Web Programming
- CS 574 Object-Oriented Analysis and Design or CS 513 Knowledge Discovery and Data Mining
Cybersecurity
Students will obtain a deep technical background in security and privacy, particularly in the cryptographic foundations of the tools that the security specialist will need to use. They will know that cryptographic tools require a deep understanding of their properties to be deployed properly, rather than simply treated as black boxes. They will obtain a background in algorithm design and implementation, and discrete mathematics for cryptography, prior to learning about the most popular cryptographic algorithms and protocols. They will also learn about both the technical and the social aspects of privacy, where legislation is still grappling with how to resolve individuals' privacy rights with the immense benefits to be gained from vast on-line information resources, and where technical solutions can inform the legal and social debate.
- CS/MA 503 Discrete Mathematics for Cryptography
- CS 578 Privacy in a Networked World
- CS 579 Foundations of Cryptography
- CS 600 Advanced Algorithm Design and Implementation
Enterprise Security and Information Assurance
This program is for students interested in security and privacy, particularly as it pertains to businesses, governments, and other forms of enterprises. They will get a basic grounding in security concepts, including the various forms of threats and defenses. Students will learn how enterprises can protect against attacks and exploits both from inside and outside the organization, including ensuring that critical data survives such attacks. Security governance is an important part of such mechanisms. They will learn how to recover from a security attack, determining the cause and sometimes the source of the exploit. Finally, students will also learn about both the technical and the social aspects of privacy, where legislation is still grappling with how to resolve individuals' privacy rights with the immense benefits to be gained from vast on-line information resources, and where technical solutions can inform the legal and social debate.
- CS 548 Enterprise Software Architecture and Design
- CS 578 Privacy in a Networked World
- CS 594 Enterprise Security and Information Assurance
- CS 573 Fundamentals of Cybersecurity or CS 506 Introduction to IT Security
Service-Oriented Computing
This program is for students who are working in an existing domain where they see the growing use of and need for IT skills. The program provides an accelerated professional education program that provides them with the skill sets that they need in order to use and manage the IT that is being deployed globally today. Students may have little or no background in software development, but they want to be a professional in a particular field with IT skills. This program will provide students with very focused training in the skill sets that are required to make them technically capable of taking existing frameworks and using them to develop new client-specific applications. The focus of the program is very much on front-end skills:
- Requirements acquisition and analysis
- Human-computer interaction
- Web design and information architecture
- Ethical and privacy issues
The kinds of tasks that students will pursue will range all the way from designing and implementing web pages, to developing distributed collaborative applications with sophisticated database back-ends using frameworks, such as Websphere and .NET.
- SOC 510/CS 545 Human-Computer Interaction
- SOC 542/CS 548 Enterprise Software Architecture and Design
- SOC 611 Fundamentals of Service Oriented Computing
- SOC 606 Introduction to Developing Internet Applications or CS 546 Web Programming or CS 549 Distributed Systems and Cloud Computing
Enterprise and Cloud Computing
This program is for students who want to become high-end IT professionals with an interest in enterprise computing. Students will learn about distributed computing from both the reliability and the security points of view. They will learn about distributed computing "in the large," including enterprise application integration and service-oriented architectures (SOA). They will build on skills learned in courses in operating systems, databases, and systems programming for enterprise computing, to learn how to administer server back-ends that are the crux of modern SOA. This will involve ensuring that applications meet their goals in terms of performance, reliability, security, and privacy. A typical backend setup will involve several virtualized servers, running heterogeneous guest operating systems on top of hypervisors, organized in a highly available cluster. Data processing and Web service applications will have service level agreements (SLAs) that must be honored. The administrator must be able to respond to performance issues by dynamically reallocating resources between applications, while at the same time responding to component failures, and potentially also security attacks.
- CS 522 Mobile Systems and Applications or CS 526 Enterprise and Cloud Computing
- CS 548 Enterprise Software Architecture and Design
- CS 549 Distributed Systems and Cloud Computing
- CS 561 ICS 594 Enterprise Security and Information Assurance
Health Informatics
Students of this program will learn to use data mining methods to derive, in an exploratory manner, valuable healthcare knowledge in terms of associations, sequential patterns, classifications, predictions and symbolic rules. They will be able to describe and use tools for preserving the privacy of confidential data, as well as explain some of the social and legal aspects of privacy. Students will be able to explain health care IT standards such as UDEF and HL7, explain health care terminology, and perform system selection and evaluation in the areas of telemedicine, dental informatics, consumer health informatics, and hospital/clinical informatics. Special attention is given to web services and mobile computing as they relate to the health care industry.
- CS 513/SOC 550 Knowledge Discovery and Data Mining
- CS 544/SOC 552 Health Informatics
- CS 548/SOC 542 Enterprise Software Architecture and Design
- CS 578/SOC 551 Privacy in a Networked World
Distributed Systems
Required courses:
- CS 521 TCP/IP Networking
- CS 549 Distributed Systems and Cloud Computing
and any two of the following courses:
- CS 511 Concurrent Programming
- CS 520 Introduction to Operating Systems
- CS 522 Mobile Systems and Applications
- CS 546 Web Programming
Computer Systems
Required courses:
- CS 514 Computer Architecture
- CS 520 Introduction to Operating Systems
plus any two of the following courses:
- CS 511 Concurrent Programming
- CS 516 Compiler Design
- CS 521 TCP/IP Networking
- CS 522 Mobile Systems and Applications
- CS 549 Distributed Systems and Cloud Computing
Computer Graphics
Required courses:
- CS 600 Advanced Algorithm Design and Implementation
- CS 537 Interactive Computer Graphics
- CS 638 Advanced Computer Graphics or CS 539 Real time Rendering, Gaming, and Simulation Programming
- CS 558 Computer Vision or CS 539 Real time Rendering, Gaming, and Simulation Programming
Multimedia Experience and Management
Required courses:
- CS 537 Interactive Computer Graphics
- SSW 540 Fundamentals of Software Engineering
- CS 545 Human Computer Interaction
- CS 538 Visual Analytics or CS 539 Real time Rendering Gaming, and Simulation Programming or CS 638 Advanced Computer Graphics
Engineer Degree
The degree of Engineer in Computer Science is for students who already have a Masters degree in computer science or a closely related field and who wish to continue to study computer science deeply at an advanced level, but who do not wish to or cannot make the time commitment necessary for the PhD degree. The degree requires 30 credits of computer science beyond the MS degree. Nine to 12 of these credits must be for a single long term project on an advanced computer science topic (course CS 950). For part time students, the project topic cannot be drawn from the student's activity. The project must be work beyond the student's job activity, so as to expand the student's sphere of expertise. The student must be advised at all times by a full time Computer Science department faculty member. The advisor must approve and supervise the project. The project must be described in a substantial document that is reviewed by a committee of faculty, presented in a public defense, and submitted to the library for archival publication.
Doctoral Program
The purpose of the Ph.D. program is to educate students for a career in computer science research. The goal is for the quality of Stevens graduates to be on par with those produced by the best Computer Science departments in the country.
Full-time study. To make progress on leading-edge subjects in a fast moving field like computer science requires full-time study. It is nearly impossible to do work that is important, timely, and novel at the pace afforded by part-time effort-either one's result will be "scooped" or conditions will change within the field, rendering the work no longer current. Accordingly, Ph.D. students will be admitted only for full-time on-campus study.
Advised study. Each doctoral student must at all times have a single advisor who is a tenured or tenure-track Stevens faculty member. The relationship between advisor and student is not merely an administrative one. Starting early in his/her career, the student will work on research projects to be determined by the advisor and student. Through this day-to-day interaction, the student will learn the form and content of high quality research. The student's advisor will also guide the student through the program, e.g., advising on such matters as which courses to take, when to attempt the qualifying exam, what dissertation topic to pursue, etc.
Advisor-advisee relationship. The department aims to admit only students whose background and interests match those of the faculty. Each admitted student will be assigned an advisor whose expertise is well matched to the student. It is hoped that most students will remain with their initial advisors throughout their career, performing research with him/her. However, the advisor-advisee relationship is a voluntary one. If either the student or the faculty member becomes dissatisfied with the relationship, then the student must seek another advisor among the faculty. A student can change advisors at any time provided that the student's new advisor is willing to accept the student.
Requirements. The Ph.D. degree requires 84 credits beyond the bachelor's degree. Students who already possess a master's degree may be granted up to 30 credits. The 84 credits may be fulfilled by some combination of: prior MS degree, enrollment in classroom courses, and enrollment in research participation (course CS 960). The division of a student's effort between classroom courses and research participation will vary from case to case, and is a decision that should be made by the student in consultation with and with the approval of the student's advisor. There is no minimum number of classroom courses for the doctorate.
Progress review. Each student's progress is reviewed by the entire computer science faculty near the end of the fall and spring semesters. Preparatory to this review, the student must submit a brief progress report describing the student's progress since the last review, as well as his/her plans for the time up to the next review. After drafting the report, the student must submit it to his/her advisor for approval. Once approved, the report must be submitted to the Computer Science department office.
Students who are doctoral "candidates" must also submit a second, separate, report to the Dean of Graduate Academics' office. The definition of the term "candidate" is left to each department, and the Computer Science department defines candidates to be students who have passed the qualifying exam, both written and oral parts. The report for the graduate dean must be submitted on a special form-the "Doctoral Activity Report," (DAR). It is acceptable to write a single report and submit the DAR to the department, as well as to the graduate office.
The outcome of the progress review meeting is that a student is placed into one of three categories: good standing, probation, or terminated. A student in good standing is making satisfactory progress toward his/her degree, and is expected to follow through on the plans outlined in his/her progress report. A student on probation is making inadequate progress toward his/her degree. A student on probation will receive a letter from the faculty that explains what remedial actions he/she must take to return to good standing, and by what time each action must be taken. No student will be terminated without spending at least the preceding semester on probation.
Qualifying Exam. Each student must pass the qualifying exam early in his/her career. The exam has two purposes: to certify that the student is broadly educated in key areas of computer science and to demonstrate that the student has become acquainted with the process of performing original research.
Accordingly, the qualifying exam has two parts, written and oral. The written portion of the qualifying exam tests the student's knowledge of fundamental computer science at an elementary level, akin to that achieved in a bachelor's program. The written exam tests three subjects: algorithms, programming languages, and operating systems. A student must pass all three subjects in order to pass the written exam. The exam is offered near the end of fall and spring semesters, timed so that grades are available at the progress review meeting. A student may take the written exam at most twice. Any subjects passed the first time need not be taken the second time. The written exam should be taken during the student's first two semesters in the program. The written exam must be completely passed during the student's first four semesters in the program.
The purpose of the oral portion of the qualifying exam is for the student to demonstrate promise in doing independent original research. The student will perform some work as specified by, and under the supervision of, his/her advisor. Ideally, this work would consist of the actual production of publishable research results; however, depending on circumstances, it may be more appropriate for the student to perform some type of pre-research work. The student will write a report detailing his/her effort and accomplishments. The student will give a public, announced talk detailing his/her effort and accomplishments. The paper will be read, and the talk attended, by the student's advisor and two other pre-selected regular Stevens faculty members. These three faculty will decide whether the student has passed the oral exam. In style, the report and the talk must be similar to research presentations given by experienced researchers. If either the report or the talk is judged to be inadequate in either content or presentation, this fact will be taken into account during the faculty's evaluation of the student that semester. The student may be terminated, placed on probation, required to prepare a new report or talk, perform further research, or some other remedial action(s).
The oral qualifying exam must be passed no more than 12 months after passage of the written qualifying exam, or by the end of student's 5th semester in the program, whichever is earlier.
Thesis proposal. To demonstrate that he/she is ready to undertake dissertation research, the student must write and present a thesis proposal. The written document must describe the proposed research so that an appropriately informed computer scientist-although not necessarily someone who is an expert in the topic-can understand the proposal. The written proposal should contain an explanation of the problem and why it is important, a sketch of the proposed solution, and background information that serves to indicate that the problem is unsolved and what prior or related approaches to this or similar problems have already been investigated. After writing the document, the student must make a public presentation of the proposed work. The document must be read-and the presentation should be attended-by the persons who are expected to form the student's dissertation defense committee. The presentation must allow reasonable time for appropriate questions by any person in attendance. After the presentation, the dissertation committee will decide whether the student's proposal indicates that he/she is ready to do the proposed work successfully.
If the proposal is judged to be inadequate in either content or presentation, this fact will be taken into account during the faculty's evaluation of the student that semester. The student may be terminated, placed on probation, required to prepare a new talk, perform further research, or some other remedial action(s).
Dissertation defense. The department follows the Stevens-wide procedures for the dissertation defense, including committee composition.
Required rate of progress. Stevens imposes certain deadlines on the student:
- Students who have a master's degree must complete the doctoral degree within six years.
- The thesis proposal must be presented at least 12 months before the degree is awarded.
- It is "recommended" that the qualifying exam be attempted no more than one year after entry to the program or after receipt of the master's degree, whichever comes first.
- In addition, a certain rate of progress through the program is typical and expected:
- The written qualifying exam should be attempted in the first two semesters.
- The written qualifying exam must be passed by the end of the fourth semester.
- The oral qualifying exam must be passed by the end of the fifth semester (or no more than 12 months after passage of the written exam, whichever is earlier).
- The thesis proposal should be presented by the end of the sixth semester.
- These are only guidelines: meeting all these targets does not necessarily constitute satisfactory progress, nor does failing to meet any necessarily constitute unsatisfactory progress.
Leave. It is expected that students, once enrolled in the doctoral program, will remain enrolled full-time without interruption until graduation. However, sometimes it is necessary for a student to take a leave for a reason, such as personal difficulty, health, etc. If such a situation arises, the student must petition the faculty in writing for a leave, which, if granted, will last for one semester. To extend the leave, a new petition must be filed. Neither indefinite leave nor excessive repetition of leave is permitted. While the student is on leave, any time limit he/she faces (e.g., completing the qualifying exam within two years) is suspended for the length of the leave.
Exceptions. The faculty reserve the right to make exceptions to any of the rules and procedures described above in order to promote and preserve the health of the doctoral program and to ensure each student's prompt and effective progress through the program.
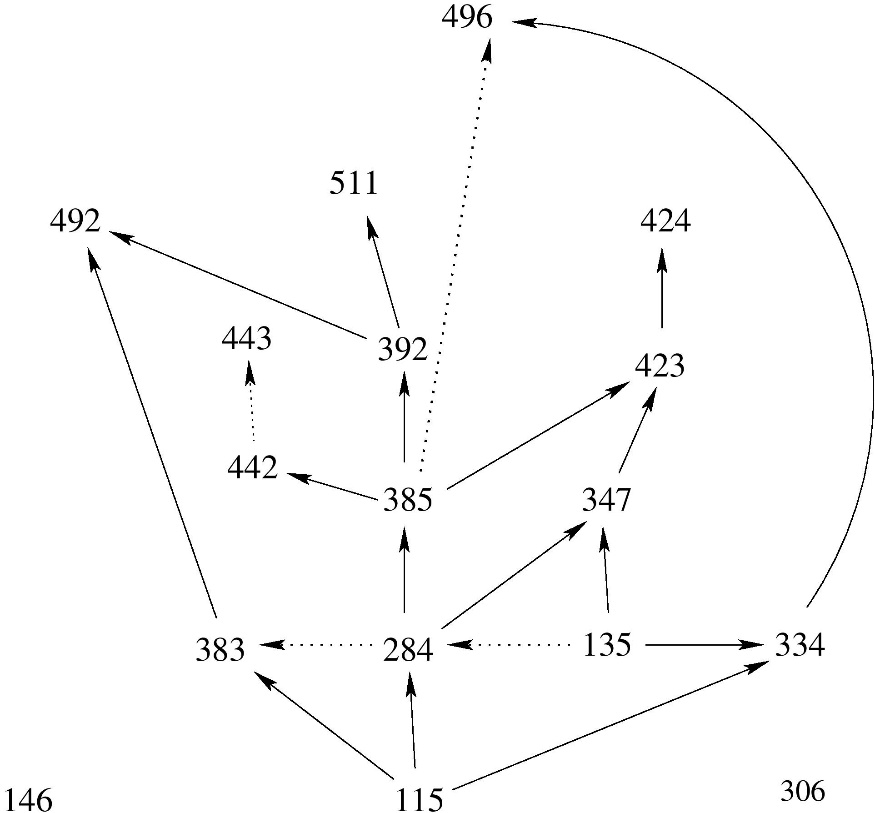
Prerequisite Diagrams
The figure below shows prerequisite and corequisite relationships among required undergraduate courses. A dashed line indicates a corequisite. For example, the dashed line from CS 135 to CS 284 means that a student taking CS 284 must either have already passed CS 135 or be taking it at the same time as CS 284. (All numbers refer to CS courses.)
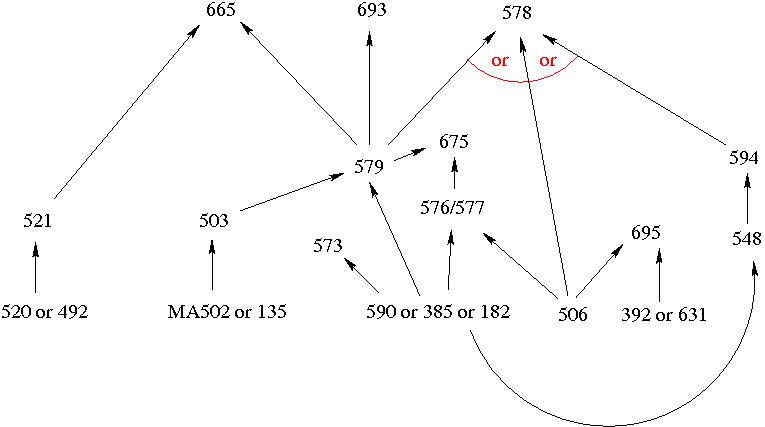
The figure below shows the prerequisite relationships among the courses in the security sub-curriculum.
Computer Science Department
Daniel Duchamp, Director
