Handbook for Windows NT Network Security by Mitun Gulati CS 800: Special Studies Spring 2000 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
1. WINDOWS NT Windows NT is on a roll. Enterprises are choosing Windows NT over Unix to host web applications for intranets, extranets and even for the public Internet. As Windows NT becomes more popular for application servers, NT administrators are concerned about security. This handbook provides a step-by-step recipe for using Windows NT security features with a layman’s description of security requirements. Windows NT security accomplish two very simple but important things:
The idea is to verify the users during logon, and authorize their access to resources. This requires a user account that defines who the users are and what they can do on the system. In a network environment, security is critical. Since users place data on servers shared with others, they expect a high level of security. You cannot install Windows NT without its advance security features. But the default securities setting that are made during the initial set up are not optimized for tight security. You must evaluate and upgrade the security settings to fit your needs. Windows NT takes advantages of features in the Intel 30836 and above processors to implement some of its security features. Protected-memory features prevent any program from accessing the code or data used by another program or by the operating system itself. Every program runs in its own protected memory. Unauthorized attempts by one program or process to access the memory of another program or process are denied by the operating system. The user account is a central theme of a Windows NT operating system. Anyone who wants access to computer or network types a user name and a password to gain access. The information about user type is checked in a user account database and holds information to verify users. If the information matches, the user is authenticated onto the network. Definition: The term Security immediately evokes the notions of:
In the most basic sense, Computer system security ensures that your computer does what it is supposed to do even if its users don't do that what they are supposed to do. It protects the information stored in it from being lost, changed whether maliciously or accidentally, or read or modified by those not authorized to access it. It tracks all access so that it knows if someone forces their way into palces they you don’t want them. After all, the lock on your front door does not keep criminals out, it leaves evidence that someone has broken in. Proper administration of system, client and server, as well as the faithful observance of related business procedure, physical access controls, and audit functions are vital in a sefcure envionment. Security means:
The US department of defense has published its security evaluation specification in Trusted Computer Security Evaluation Criteria (TCSEC), which is often called "Orange Book". The Orange Book defines four broad hierarchical division of security protection in increasing order of trust, they are.
Each division consists of one or more numbered classes, with higher numbers indicating a greater degree of security.
All networked facilities, system and data are classified according to their sensitivity to disclosure and their mission critically. Following is the security classification.
Here, I will not discuss in detail each of this classification, as this is not my main topic of concern. According to Matthew Sterbe in the NT network security, the security zones are:
The object of computer security is to control Who has access to What. The Who in the case of computer security are those network users with access, and everyone else to whom you wish to restrict access. The What are the resources on your network including files, directories, printers etc. A computer operating system that has good security mechanism does the following:
3. The Evolution of Windows NT Server The most notable design objectives for Windows NT were and still are:
Logon as the Administrator (or a member of the Administrators group) and perform the following
It is also possible to configure auditing on a file/directory. Right click on the file/directory, select properties, and select the security tab and then select auditing How do I view/clear the security log Logon as the Administrator (or a member of the Administrators group) and perform the following
How can I copy files and keep their security and permissions? By default when you copy files from one NTFS partition to another, the files inherit their protections from the parent directory. It is possible to copy the files and keep their settings using the SCOPY program that comes with the NT resource kit. SCOPY can copy owner and security audit information: SCOPY c:\savilltech\secure.dat
d:\temp\ /o /a Note: Both the origin and target drives must be NTFS or the command will fail. How do I enable auditing on certain files/directories? Auditing is only available on NTFS volumes. Follow the instructions below:
Note: You must ensure that File access auditing is enabled (Start - Programs - Administrative Tools - User Manager - Policies - Audit). These events can then be viewed using the Event Viewer (Start - Programs - Administrative Tools - Event Viewer - Log - Security) How can I configure the system to stop when the security log is full? To avoid security logs being lost you can configure the system to halt if the security log becomes full so that only Administrators can logon, they can then archive the log and purge
When this happens the OS will display a BSOD How can I clear the pagefile at shutdown? As pagefile contains areas of memory that were swapped out to disk, it may be in a secure environment you want this pagefile cleared when the machine is shutdown as parts of memory containing passwords/sensitive information may have been mapped out to the pagefile.
How do I enable strong password filtering? Windows NT 4.0 introduced a password filter, passfilt.dll, which implements the following new restrictions
To enable this functionality perform the following on all PDC's (and stand alone's if used). You do not need to install this on BDC's, however you should in case the BDC is promoted to a PDC.
It should be noted you will still be able to set passwords in User Manager that do not meet the criteria, this is by design as direct SAM updates are not filtered.
How can I restrict access to objects from Anonymous accounts? It is possible to restrict the ability to list domain user names and enumerate share names available to anonymous logon users (also known as NULL session connections). If you feel this is a security risk Windows NT 4.0 introduces an option to stop anonymous users listing users and shares. To enable this perform the following:
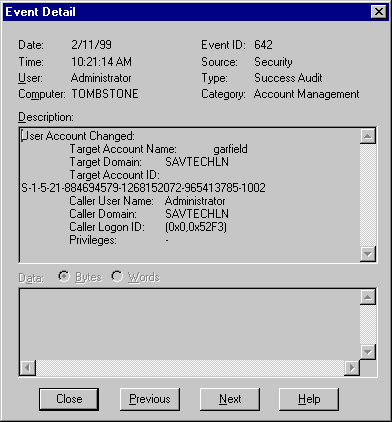
What is a SID (Security ID)? SID stands for Security Identifier and is used within NT/2000 as a value to uniquely identify an object such as a user or a group. The SID assigned to a user becomes part of the access token, which is then attached to any action attempted or process executed by that user or group. If a duplicate SID did exist then all users with this SID would authenticate as what would be seen as the same user. It is possible for cloned machines to have the same SID, which would be seen by the authentication mechanism as the same machine. The SID under normal operation will be unique and will identify an individual object such as a user, group or a machine. A SID contains:
For example: S-1-5-21-917267712-1342860078-1792151419-500
5. TIPS Always use NTFS disk partition instead of FAT. NTFS offers security features and FAT
doesn't - You won't be able to set any access permissions for files and directories on
that drive. Make sure that all of NT's password features have been implemented. This requiring users
to have strong passwords, changing it at regular intervals. Default Administrator account is a target for most intruders. Create a new admin account
and take away all permissions from the existing admin account. Do this by creating a new user, add him to the administrator group and duplicate all
account policies and permissions granted to the default admin. After that revoke all the
permissions from the default admin. But do leave it enabled, this way intruders won't know
its crippled until they take the time to actually crack the account. Enable Auditing on all NT systems Be careful about NT domain trusts Block all non-essential TCP/IP ports, both inbound and outbound. Delete or disable unused accounts. Make sure the user do not leave their NT workstation turned on and unattended. Remove or disable the guest account. Don't run services you don't actually need. 6. Windows NT Server Attacks and Defenses As its usage across business and industry increases, Windows NT server has come under closer scrutiny than ever regarding possible security flaws and holes. In the following table, we examine the various attacks on the Windows NT Server operating system and the defenses put in place in attempts to mitigate them. Windows NT has been shown vulnerable to various Denial of Service (DOS) and other attacks that either attempt to retrieve sensitive information or attempt to gain access with permissions greater that the attackers own. To provide a secure environment, Microsoft provides fixes in the form of patches and service packs. After being notified of the exposure presented, Microsoft issues fixes. Listed below are some of the more widespread attacks that have been identified and the associated fix that has been released.
Windows NT Server utilizes an integrated architecture to authenticate, validate and record information about security within the operating system. The security architecture consists of several components:
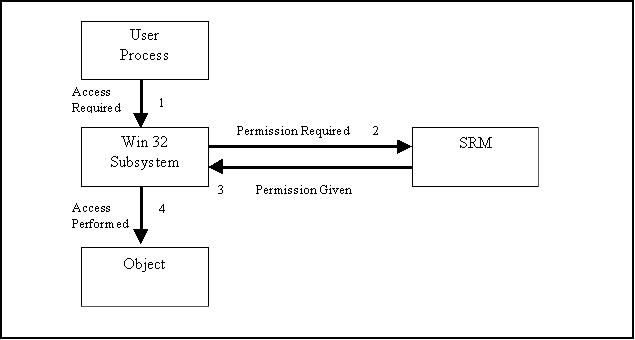
The overall system architecture is divided into two main areas: the kernel and user. These are shown in the diagram. The segments of the architecture that relate to security: Security Reference Monitor, Security Subsystem and the Logon Process; are highlighted on the diagram. Within this architecture, Windows NT is able to apply security to every object and process it controls. This means that every object resident on the Windows NT computer and every process running on that computer are subject to the security controls of the overall architecture.
1.) Security Reference Monitor The Security Reference Monitor (SRM) is part of the NT Executive within the NT Kernel as shown in diagram, with the security functions highlighted in gray. It is responsible for enforcing all accesses validation and audit policies defined within the Local Security Authority. In this way, the SRM is designed to protect all system objects from unauthorized access or modification. The SRM is the repository for the system’s access validation code and is the only copy of that code on any given Windows NT system. This ensures that all protection is provided uniformly to objects on the system. The SRM provides services for validating access to objects, generating audit messages that are subsequently logged by the Local Security Authority, and verifying user accounts for the appropriate privileges.
The Local Security Authority (LSA) provides many services to the security subsystem of the Windows NT operating system. It is designed to ensure that the user has permission to access the system by validating the user logon. It manages the local security policy as set by the administrator; it generates access tokens, and provides interactive validation services when access is requested for any system object. The LSA also controls the audit policy, set by the administrator, and writes any messages generated by the Security Reference Monitor to the event logs. The Security Account Manager (SAM) controls and maintains the Security Account Database (SAD). The SAD is part of the registry and is invisible to the users during normal processing. The SAD contains account information for all user and group accounts. The SAM provides the user validation service during logon that is used by the LSA. It compares the cryptographic hash of the password given at logon time with the hashed password stored in the SAD. It will then provide the user’s Security Identifier (SID), as well as the SIDs for any group the user belongs to, back to the LSA for the creation of the access token that will be used during that session. The Windows NT logon process, which is diagrammed in figure, is mandatory for initiating a session with a Windows NT server or workstation. The logon process differs slightly if the user is attempting to logon to a local machine or to a remote server in a network. The logon is a multi-step process that the following list. The numbers that follow the steps match the step with pictures included in figure. Local Machine Logon
5.) Discretionary Access Controls Discretionary Access Controls (DAC) provide object and resource owners the means to control whom can access resources as well as how much access they may have. Access to system resources, such as files, directories and folders, printers, network shares, and system services; can be controlled either through GUI-based system tools or through the command line. Objects in Windows NT support discretionary access controls. The NT Explorer, Print Manager, User Manager for Domains, and Server Manager are tools used to manipulate DACs on the common objects that users and administrators work with in the Windows NT environment. Objects within a Windows NT system may have an Access Control List. Access Control Lists (ACL) are lists of users and groups that have some level of permissions to access or operate an object. Each object in the Windows NT system contains a security descriptor, which is comprised of the Security Identifier of the person who owns the object, the regular ACL for access permissions, the system ACL (SACL) which is used for auditing, and a group security identifier. ACLs may be composed of Access Control Entries (ACE). There are situations where an ACL will have no ACEs. This is known as a null or empty ACL. Each ACE describes the permissions for each user or group that has access to an object. Access Control Entries within Windows NT are composed of permission categories known as either standard or special. Each permission type is valid for both files and directories. Special permissions consist of the six individual permissions, while the Standard permissions are combinations derived from the special permissions. These permission levels include No Access, a level of authority that may supersede all other authorities
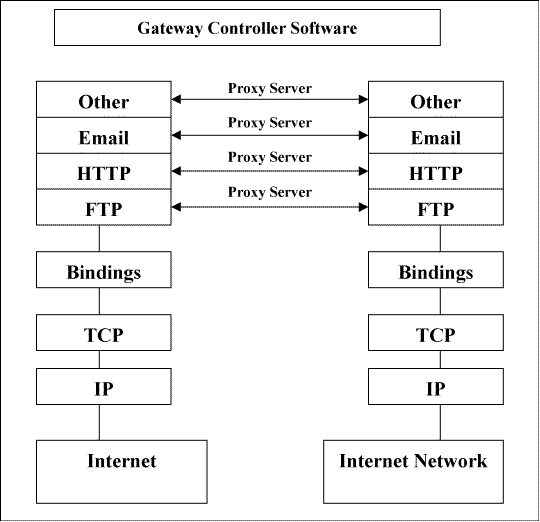
A firewall is a set of related programs, located at a network gateway server, that protects the resources of a private network from users from other networks. (The term also implies the security policy that is used with the programs.) An enterprise with an intranet that allows its workers access to the wider Internet installs a firewall to prevent outsiders from accessing its own private data resources and for controlling what outside resources its own users have access to.
A firewall, as shown above, puts up a barrier that controls the flow of traffic between networks. The safest firewall would block all traffic, but that defeats the purpose of making the connection, so you need to strictly control selected traffic in a secure way. The highest level of protection today is provided by application-level proxy servers. Here, proxy services run at the application level of the network protocol stack for each different type of service (FTP, HTTP, etc.). A proxy server is a component of a firewall that controls how internal users access the outside world (the Internet) and how Internet users access the Internal network. In some cases, the proxy blocks all outside connections and only allows internal users to access the Internet. The only packets allowed back through the proxy are those that return responses to requests from inside the firewall. In other cases, both inbound and outbound traffic are allowed under strictly controlled conditions. Note that a virtual "air-gap" exists in the firewall between the inside and outside networks and that the proxies bridge this gap by working as agents for internal or external users. What are proxy servers and how do they work? A proxy server (sometimes referred to as an application gateway or forwarder) is an application that mediates traffic between a protected network and the Internet. Proxies are often used instead of router-based traffic controls, to prevent traffic from passing directly between networks. Many proxies contain extra logging or support for user authentication. Since proxies must ``understand'' the application protocol being used, they can also implement protocol specific security (e.g., an FTP proxy might be configurable to permit incoming FTP and block outgoing FTP). Proxy servers are application specific. In order to support a new protocol via a proxy, a proxy must be developed for it. One popular set of proxy servers is the TIS Internet Firewall Toolkit (``FWTK'') which includes proxies for Telnet, rlogin, FTP, X-Window, HTTP/Web, and NNTP/Usenet news. SOCKS is a generic proxy system that can be compiled into a client-side application to make it work through a firewall. Its advantage is that it's easy to use, but it doesn't support the addition of authentication hooks or protocol specific logging How do I make FTP work through my firewall? Generally, making FTP work through the firewall is done either using a proxy server or by permitting incoming connections to the network at a restricted port range. The FTP client is then modified to bind the data port to a port within that range. This entails being able to modify the FTP client application on internal hosts.
|